http://thehackernews.com/2015/03/freak-openssl-vulnerability.html
- See more at: http://thehackernews.com/2015/03/freak-openssl-vulnerability.html#sthash.YELPZFms.dpuf
- See more at: http://thehackernews.com/2015/03/freak-openssl-vulnerability.html#sthash.YELPZFms.dpuf
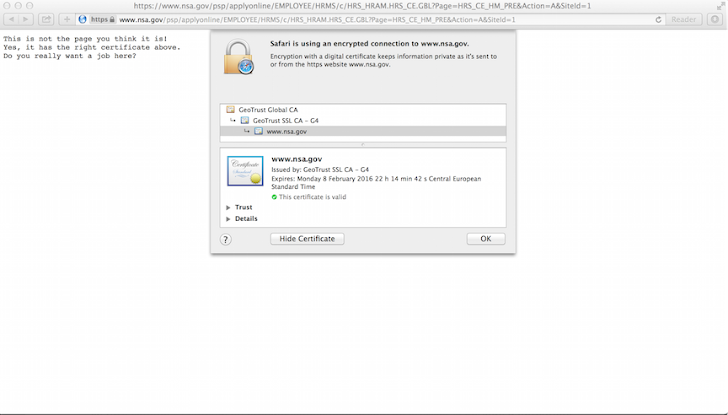
Another new widespread and disastrous SSL/TLS vulnerability has been uncovered that for over a decade left Millions of users of Apple and Android devices vulnerable
to man-in-the-middle attacks on encrypted traffic when they visited
supposedly 'secured' websites, including the official websites of the
White House, FBI and National Security Agency.
Dubbed the "FREAK" vulnerability (CVE-2015-0204) - also known as Factoring Attack on RSA-EXPORT Keys
- enables hackers or intelligence agencies to force clients to use
older, weaker encryption i.e. also known as the export-grade key or
512-bit RSA keys.
FREAK vulnerability discovered by security researchers of French
Institute for Research in Computer Science and Automation (Inria) and
Microsoft, resides in OpenSSL versions 1.01k and earlier, and Apple's
Secure Transport.
90s WEAK EXPORT-GRADE ENCRYPTION
Back in 1990s, the US government attempted to regulate the export of
products utilizing "strong" encryption and devices were loaded with
weaker "export-grade" encryption before being shipped out of the
country.
At that time, it was allowed a maximum key length of 512 bits for
"export-grade" encryption. Later in 2000, with the modification of the
US export laws, vendors were able to include 128-bit ciphers in their
products and were able to distribute these all over the world.
The only problem is that "export-grade" cryptography support was never
removed and now three decades later, FREAK vulnerability make it
significantly easier for hackers to decode the website’s private key and
decrypt passwords, login cookies, and other sensitive information from
HTTPS connections.
HOW FREAK VULNERABILITY WORKS ?
Assistant Research Professor Matthew Green of Johns Hopkins University's
Information Security Institute in Maryland summarizes the FREAK
vulnerability in a blog post detailing how a hacker could perform MitM attack:
- In the client's Hello message, it asks for a standard 'RSA' ciphersuite.
- The MITM attacker changes this message to ask for 'export RSA'.
- The server responds with a 512-bit export RSA key, signed with its long-term key.
- The client accepts this weak key due to the OpenSSL/Secure Transport bug.
- The attacker factors the RSA modulus to recover the corresponding RSA decryption key.
- When the client encrypts the 'pre-master secret' to the server, the attacker can now decrypt it to recover the TLS 'master secret'.
- From here on out, the attacker sees plain text and can inject anything it wants.
36% SSL WEBSITES VULNERABLE TO HACKERS
A scan of more than 14 million websites that support the SSL/TLS
protocols found that more than 36% of them were vulnerable to the
decryption attacks that support RSA export cipher suites (e.g., TLS_RSA_EXPORT_WITH_DES40_CBC_SHA).
Cracking a 512-bit key back in the '90s would have required access to
supercomputers of that time, but today, it can be done in seven hours
and cost nearly $100 per website only.
It is possible to carry out FREAK vulnerability attack when a user
running a vulnerable device — currently includes Android smartphones,
iPhones and Macs running Apple's OS X operating system — connects to a
vulnerable HTTPS-protected website. At the moment, Windows and Linux
end-user devices were not believed to be affected.
'FREAK' VULNERABILITY SIMILAR TO 'POODLE'
FREAK vulnerability is similar to last year's POODLE flaw or
Padding Oracle On Downgraded Legacy Encryption, which allowed hackers
to downgrade the entire SSL/TLS Internet-communication security suite to
the weakest possible version. FREAK affects only those SSL/TLS
implementations that accept export versions of protocols that use the
RSA encryption algorithm.
Security researchers are maintaining a list of top vulnerable websites and
encourage web server administrators to disable support for export
suites, including all known insecure ciphers, and enable forward
secrecy.
You can also use an Online SSL FREAK Testing Tool to check whether a website is vulnerable or not.
You can also use an Online SSL FREAK Testing Tool to check whether a website is vulnerable or not.
APPLE AND GOOGLE PLANS TO FIX FREAK
Google said an Android patch has already been distributed to partners.
Meanwhile, Google is also calling on all websites to disable support for
export certificates.
Apple also responded to the FREAK vulnerability and released a statement
that, "We have a fix in iOS and OS X that will be available in software
updates next week."
Another new widespread and disastrous SSL/TLS vulnerability has been uncovered that for over a decade left Millions of users of Apple and Android devices vulnerable
to man-in-the-middle attacks on encrypted traffic when they visited
supposedly 'secured' websites, including the official websites of the
White House, FBI and National Security Agency.
Dubbed the "FREAK" vulnerability (CVE-2015-0204) - also known as Factoring Attack on RSA-EXPORT Keys
- enables hackers or intelligence agencies to force clients to use
older, weaker encryption i.e. also known as the export-grade key or
512-bit RSA keys.
FREAK vulnerability discovered by security researchers of French
Institute for Research in Computer Science and Automation (Inria) and
Microsoft, resides in OpenSSL versions 1.01k and earlier, and Apple's
Secure Transport.
90s WEAK EXPORT-GRADE ENCRYPTION
Back in 1990s, the US government attempted to regulate the export of
products utilizing "strong" encryption and devices were loaded with
weaker "export-grade" encryption before being shipped out of the
country.
At that time, it was allowed a maximum key length of 512 bits for
"export-grade" encryption. Later in 2000, with the modification of the
US export laws, vendors were able to include 128-bit ciphers in their
products and were able to distribute these all over the world.
The only problem is that "export-grade" cryptography support was never
removed and now three decades later, FREAK vulnerability make it
significantly easier for hackers to decode the website’s private key and
decrypt passwords, login cookies, and other sensitive information from
HTTPS connections.
HOW FREAK VULNERABILITY WORKS ?
Assistant Research Professor Matthew Green of Johns Hopkins University's
Information Security Institute in Maryland summarizes the FREAK
vulnerability in a blog post detailing how a hacker could perform MitM attack:
- In the client's Hello message, it asks for a standard 'RSA' ciphersuite.
- The MITM attacker changes this message to ask for 'export RSA'.
- The server responds with a 512-bit export RSA key, signed with its long-term key.
- The client accepts this weak key due to the OpenSSL/Secure Transport bug.
- The attacker factors the RSA modulus to recover the corresponding RSA decryption key.
- When the client encrypts the 'pre-master secret' to the server, the attacker can now decrypt it to recover the TLS 'master secret'.
- From here on out, the attacker sees plain text and can inject anything it wants.
36% SSL WEBSITES VULNERABLE TO HACKERS
A scan of more than 14 million websites that support the SSL/TLS
protocols found that more than 36% of them were vulnerable to the
decryption attacks that support RSA export cipher suites (e.g., TLS_RSA_EXPORT_WITH_DES40_CBC_SHA).
Cracking a 512-bit key back in the '90s would have required access to
supercomputers of that time, but today, it can be done in seven hours
and cost nearly $100 per website only.
It is possible to carry out FREAK vulnerability attack when a user
running a vulnerable device — currently includes Android smartphones,
iPhones and Macs running Apple's OS X operating system — connects to a
vulnerable HTTPS-protected website. At the moment, Windows and Linux
end-user devices were not believed to be affected.
'FREAK' VULNERABILITY SIMILAR TO 'POODLE'
FREAK vulnerability is similar to last year's POODLE flaw or
Padding Oracle On Downgraded Legacy Encryption, which allowed hackers
to downgrade the entire SSL/TLS Internet-communication security suite to
the weakest possible version. FREAK affects only those SSL/TLS
implementations that accept export versions of protocols that use the
RSA encryption algorithm.
Security researchers are maintaining a list of top vulnerable websites and
encourage web server administrators to disable support for export
suites, including all known insecure ciphers, and enable forward
secrecy.
You can also use an Online SSL FREAK Testing Tool to check whether a website is vulnerable or not.
You can also use an Online SSL FREAK Testing Tool to check whether a website is vulnerable or not.
APPLE AND GOOGLE PLANS TO FIX FREAK
Google said an Android patch has already been distributed to partners.
Meanwhile, Google is also calling on all websites to disable support for
export certificates.
Apple also responded to the FREAK vulnerability and released a statement
that, "We have a fix in iOS and OS X that will be available in software
updates next week."
Subscribe to Quick News Updates
Another new widespread and disastrous SSL/TLS vulnerability has been uncovered that for over a decade left Millions of users of Apple and Android devices vulnerable
to man-in-the-middle attacks on encrypted traffic when they visited
supposedly 'secured' websites, including the official websites of the
White House, FBI and National Security Agency.
Dubbed the "FREAK" vulnerability (CVE-2015-0204) - also known as Factoring Attack on RSA-EXPORT Keys
- enables hackers or intelligence agencies to force clients to use
older, weaker encryption i.e. also known as the export-grade key or
512-bit RSA keys.
FREAK vulnerability discovered by security researchers of French
Institute for Research in Computer Science and Automation (Inria) and
Microsoft, resides in OpenSSL versions 1.01k and earlier, and Apple's
Secure Transport.
90s WEAK EXPORT-GRADE ENCRYPTION
Back in 1990s, the US government attempted to regulate the export of
products utilizing "strong" encryption and devices were loaded with
weaker "export-grade" encryption before being shipped out of the
country.
At that time, it was allowed a maximum key length of 512 bits for
"export-grade" encryption. Later in 2000, with the modification of the
US export laws, vendors were able to include 128-bit ciphers in their
products and were able to distribute these all over the world.
The only problem is that "export-grade" cryptography support was never
removed and now three decades later, FREAK vulnerability make it
significantly easier for hackers to decode the website’s private key and
decrypt passwords, login cookies, and other sensitive information from
HTTPS connections.
HOW FREAK VULNERABILITY WORKS ?
Assistant Research Professor Matthew Green of Johns Hopkins University's
Information Security Institute in Maryland summarizes the FREAK
vulnerability in a blog post detailing how a hacker could perform MitM attack:
- In the client's Hello message, it asks for a standard 'RSA' ciphersuite.
- The MITM attacker changes this message to ask for 'export RSA'.
- The server responds with a 512-bit export RSA key, signed with its long-term key.
- The client accepts this weak key due to the OpenSSL/Secure Transport bug.
- The attacker factors the RSA modulus to recover the corresponding RSA decryption key.
- When the client encrypts the 'pre-master secret' to the server, the attacker can now decrypt it to recover the TLS 'master secret'.
- From here on out, the attacker sees plain text and can inject anything it wants.
36% SSL WEBSITES VULNERABLE TO HACKERS
A scan of more than 14 million websites that support the SSL/TLS
protocols found that more than 36% of them were vulnerable to the
decryption attacks that support RSA export cipher suites (e.g., TLS_RSA_EXPORT_WITH_DES40_CBC_SHA).
Cracking a 512-bit key back in the '90s would have required access to
supercomputers of that time, but today, it can be done in seven hours
and cost nearly $100 per website only.
It is possible to carry out FREAK vulnerability attack when a user
running a vulnerable device — currently includes Android smartphones,
iPhones and Macs running Apple's OS X operating system — connects to a
vulnerable HTTPS-protected website. At the moment, Windows and Linux
end-user devices were not believed to be affected.
'FREAK' VULNERABILITY SIMILAR TO 'POODLE'
FREAK vulnerability is similar to last year's POODLE flaw or
Padding Oracle On Downgraded Legacy Encryption, which allowed hackers
to downgrade the entire SSL/TLS Internet-communication security suite to
the weakest possible version. FREAK affects only those SSL/TLS
implementations that accept export versions of protocols that use the
RSA encryption algorithm.
Security researchers are maintaining a list of top vulnerable websites and
encourage web server administrators to disable support for export
suites, including all known insecure ciphers, and enable forward
secrecy.
You can also use an Online SSL FREAK Testing Tool to check whether a website is vulnerable or not.
You can also use an Online SSL FREAK Testing Tool to check whether a website is vulnerable or not.
APPLE AND GOOGLE PLANS TO FIX FREAK
Google said an Android patch has already been distributed to partners.
Meanwhile, Google is also calling on all websites to disable support for
export certificates.
Apple also responded to the FREAK vulnerability and released a statement
that, "We have a fix in iOS and OS X that will be available in software
updates next week."
Subscribe to Quick News Updates

Comments
Post a Comment